Simplifying Password Management
Many folk become shipwrecked while navigating the oceanic minefield of password guidance. Advice typically emphasizes using long and complex passwords, without explaining the practicalities of how to realistically achieve this.
Password management (creating, using and updating passwords) is an area where I’ve attempted to give a helping hand in my volunteering capacity with the elderly / unskilled. I’m passionate that satisfactory password outcomes can be accomplished without needing:
- Technical skills akin to those of a rocket scientist
- Passwords resembling ancient Egyptian hieroglyphics
- Memory recollection comparable to that of an elephant
The following video demonstrates a password management system which I’ve named magic numbers. It describes a secure method for writing passwords down on paper or typing them into an electronic document. Following the magic number approach enables good enough security for almost anyone. My use of this phrase isn’t indicative of trivialising the subject matter, it simply emphasizes the approach as being fit for purpose for folk who might otherwise resort to using the same password for multiple accounts.
I wrote a short instruction guide explaining the magic numbers approach, I’ve tried my utmost to make it as readable / accessible as possible. The video and instruction guide describe the potential for digitally recording passwords using a word processor or spreadsheet. I also describe how they could simply be written on paper, the following scanned table indicates what a written table containing passwords incorporating a ‘magic number’ (in this case the number 7) might look like.
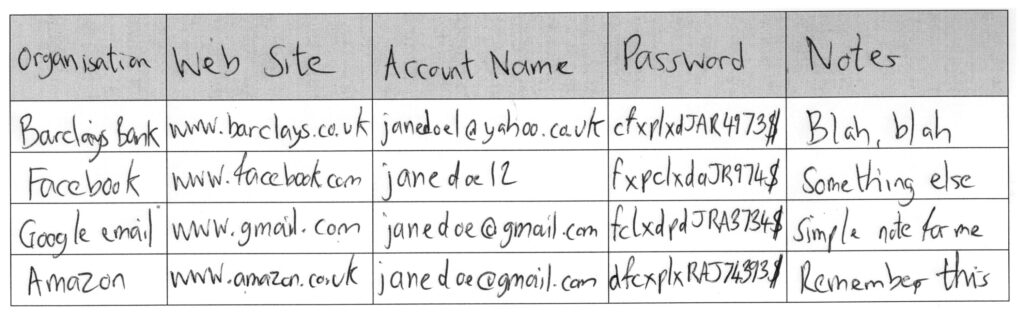
The UK National Cyber Security Centre, who are a part of GCHQ, has an elegantly explained approach regarding high value passwords which goes by the name of three random words. While GCHQ deals with the UK’s nation-state and counter-terrorism threats, NCSC deals with a wider digital landscape, such as government agencies, private businesses and the general public. I asked NCSC to review my magic number idea, and although they’re unable to endorse third parties, they were nice enough to email me a pat on the back.
Renowned UK based IT security journalist, Davey Winder, wrote positively about magic numbers for a PC Pro article in November 2022 (Issue 337).

bitwarden Password Management Tutorial Video
Q. Why use a password manager? A. You need to create strong and unique passwords for every account, but remembering them all without help gets tricky.
The following video tutorial is for folk who are a step forward from my ‘magic number’ guidance, and want pragmatic guidance on the use of a password manager application. After using a particular password manager for several years, I freshly explored the plethora of products available, paying much attention to reviews by respected organisations and professionals. I chose a product named bitwarden, due to it being focussed on essential features, aligned with ease of use – and it being free! By picking a new product, I was able to experience a little of the learning curve which any new user of a different application experiences.
While I feel confident in personally recommending bitwarden, it’s worthwhile considering independent expert reviews to guide you in your choice of the best password manager for your circumstances. To this end, I’d suggest www.passwordmanager.com, it’s an organisation whose mission is to gather information on the various password managers available and summarise / report on them, as well giving competitive analysis of one application versus another – this is my personal favourite bitwarden review. Finally, Bitwarden has amalgamated numerous reviews onto a single reference page.
The transcript which I used when narrating the video can be downloaded as a PDF for use as a reference guide.
Headway Charity
During the COVID-19 lockdowns of 2020 and 2021, I participated in ‘Zoom video chats’ with the Headway charity organisation. I took the opportunity to give presentations based largely on the content of the magic numbers concept. I realised that while my explanations were conceptually valid, they didn’t describe matters for my audience as simply or as clearly as I’d intended. I made an extra (simpler) video to reflect this, which can be viewed via my Headway page.
Krysalis
I collaborated with Krysalis Consultancy (neuro-occupational therapy specialists) to come up with an impactful introduction to my magic numbers approach – see bottom of the linked page.
Web Browser Cookies
Introduction
When accessing a website with a browser for the first time, you’re often presented with a choice in regards to cookies along the lines of:
- Configure settings
- Allow all cookies
The former option typically results in a barrage of jargon, which is different for every website accessed and only a realistic choice for the technically proficient. The second option feels like a lazy and insecure approach, which you imagine you should avoid. The cookie dilemma choice could be summarised as choosing between a rock and a hard place. 😢 I propose a solution which enables you to select the allow all cookies choice, but still maintain a satisfactory security / privacy posture.
Before going further, I should provide a little balance to the cookie narrative. For websites which you repeatedly access, cookies are helpful in recording settings and preferences. Examples of such are the location you’ve picked for a weather forecast, and personalisation you’ve configured on web sites you’ve accessed, in the vein of layout style and content preferences. Cookies are also used to record matters like the username you submitted when logging on at a website. For websites which you use regularly, cookies provide significant benefits which you’ll want to make use of.
Proposed Solution – Dual Browsers
I propose two distinct browsers to be used for web surfing activity:
- Primary (existing) browser
- Secondary (additional) browser
Your primary browser, for example Google Chrome or Microsoft Edge or Apple Safari or Mozilla Firefox, would be used to access everyday, familiar web sites used for shopping, banking, email and social media, etc.
I then recommend installing a secondary browser to be used for accessing all new websites and performing web searches, e.g. via google.com or duckduckgo.com (my personal choice). The secondary browser should be configured as the default browser, such that email links open in it. It’d have its security / privacy settings configured to ensure that all material is deleted when it’s closed, such that it doesn’t become clogged up with history and tracking material (cookies) for websites which may only be visited once. It’s empowering when presented with a cookie choice by a new website to click “Yes” without giving it much more thought.
Important – the secondary browser approach doesn’t entirely negate the need to be vigilant when clicking email links, or links on unfamiliar websites, as these can still be harmful. If you are in any way concerned with having accessed a page on an unexpected website, it’s necessary to immediately close the secondary browser and commence browsing activity afresh. When you find yourself accessing a trustworthy new website on a repeated basis in the secondary browser, you simply change tack going forwards to opening it in your primary browser, and perhaps bookmarking it.
Demonstration Video
Practical Guidance
I personally recommend using DuckDuckGo as the secondary browser app on mobile devices, and Brave on Windows desktops. However, most suitably configured browsers can be chosen. The links below provide download guidance for the aforementioned secondary browser suggestions:
- DuckDuckGo on Apple iPads and iPhones
- DuckDuckGo on Android smartphones and tablets
- Brave Windows desktops
I’ve written instructions for setting DuckDuckGo as the default app on mobile devices, as well as configuring it to purge cookies / browsing history upon exit – it can be downloaded as a PDF. The instructions contain similar guidance for using the Brave browser on Windows desktops.
Pictorial Demonstration
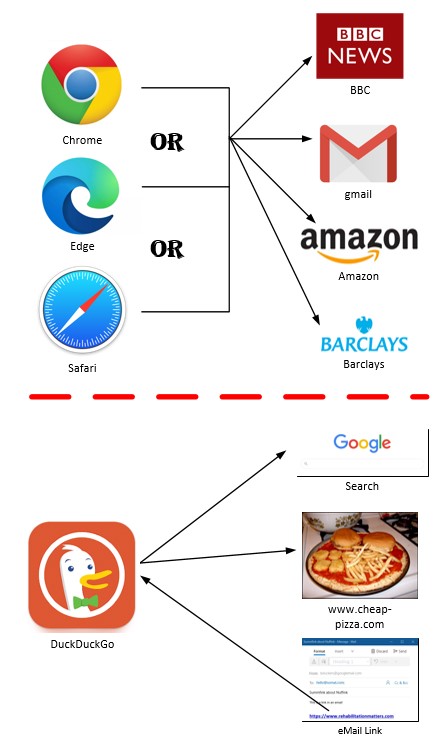
The following graphic illustrates how:
- Browsing to familiar websites would be performed in the primary browser
- Web searches and accessing new websites would be done with the secondary browser
Value Pyramid
While considering internet security in a general context, I believe the strongest weapon everyone possesses in dealing with digital threats is common sense. When browsing the world wide web, if something doesn’t feel quite right, stop it or ignore it and move onto something else, you can then forget about it in five seconds flat.
As far as financial enticements are concerned, I believe in what I call the value pyramid whenever a marketing campaign implies I can make lots of money.
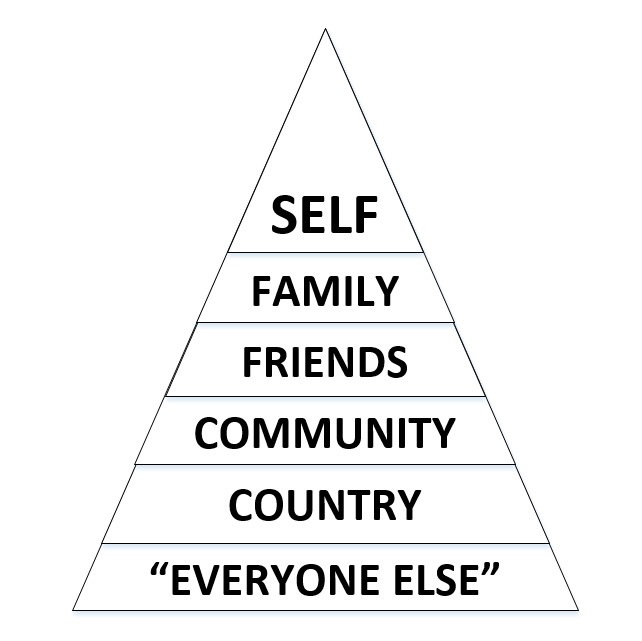
If any person or organisation had knowledge of a simple, risk free method of making lots of money, they’d observe the value pyramid rather than go out to the great worldwide mass of unknown folk. By way of example – if you knew of some get rich quick magic dust, I wouldn’t expect any of it to be sprinkled in my direction. 🙂
